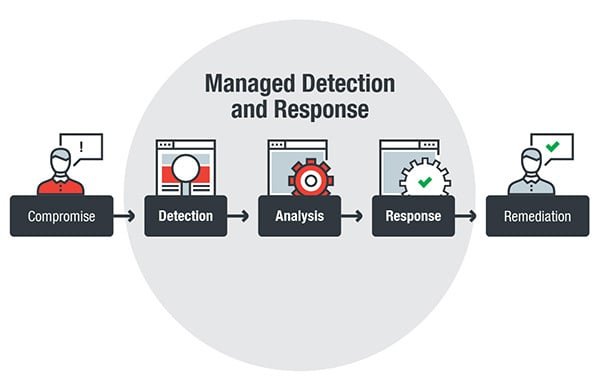
Threat Detection and Response (TDR) is a powerful collection of advanced malware defense tools that correlate threat indicators from Firebox appliances and Host Sensors to stop known, unknown and evasive malware threats.
Hackers are designing malware to be more sophisticated than ever. Through packing, encryption, and polymorphism, cyber criminals are able to disguise their attacks to avoid detection. Zero day threats and advanced malware easily slip by antivirus solutions that are simply too slow to respond to the constant stream of emerging threats.
Organizations of all sizes need a solution that leverages a holistic approach to security from the network to the endpoint.